The EigenLayer ecosystem has emerged as a crucial driver of innovation and expanding the capabilities of the Ethereum network. As a leading node operator, we have taken a strategic, Safety over Speed approach to identifying and onboarding some of the most exciting Actively Validated Services (AVSs) that are set to transform the industry.
Let's dive into the first batch of EigenLayer AVSs that Chorus One is registering:
1. EigenDA: Scaling Data Availability for Rollups [Onboarded]
At the heart of the scalability challenges faced by Ethereum lie the complexities of data availability. EigenDA aims to tackle this problem head-on by providing a secure and scalable data availability solution for optimistic and zero-knowledge (ZK) rollups. By leveraging the restaking primitive developed by EigenLabs, EigenDA empowers rollups to access lower transaction costs, higher throughput, and robust security across the EigenLayer ecosystem.
Why we onboarded EigenDA: As the first AVS to launch on the EigenLayer mainnet, and its impressive $1 billion in total value locked (TVL), we see immense potential in supporting EigenDA and positioning it as a preferred solution for leading Layer 2 ecosystems, including the OP Stack.
2. Brevis: Trustless Co-Processing for Data-Rich Applications [Onboarded]
Brevis belongs to a class of solutions that thrive within the EigenLayer ecosystem – co-processor networks. These specialized networks extend the functionality of a stack to handle computationally intensive tasks, such as verifying complex data points for decentralized applications (dApps).
Brevis tackles the challenge of "data-rich" use cases, where retrieving and validating on-chain data can be both time-consuming and costly. By leveraging a novel "propose-challenge" model, Brevis generates ZK proofs to ensure the accuracy of its results, empowering applications in DeFi, user-segment optimization, and beyond to operate in a truly trustless manner.
Why we onboarded Brevis: Our decision to onboard Brevis as its second AVS was driven by the project's open-source codebase and the alignment with the team's vision. As a modular and efficient solution, Brevis aligns perfectly with Chorus One's commitment to driving innovation and supporting the growth of the decentralized ecosystem.
3. Eoracle: Bringing Transparency and Security to Oracle Networks
One of the biggest hurdles in the crypto industry has been the "oracle problem" – the challenge of reliably and securely bringing real-world data onto blockchain networks. Eoracle aims to address this issue by creating an Ethereum-native oracle solution that leverages the decentralization, transparency, and security of the Ethereum network.
Why are we onboarding Eoracle: As the "Data Validator" AVS operated by Chorus One, Eoracle connects node operators to compute, validate, and publish off-chain data to dApps in a secure and trustless manner. By tapping into the Ethereum validator set through EigenLayer, Eoracle represents a crucial step towards building a more robust and reliable oracle infrastructure for the decentralized ecosystem.
4. Lagrange: Cryptographically secured proofs for the Multichain Future
Inspired by Ethereum’s Sync Committee, Lagrange’s State Committee seeks to provide a robust, scalable, and shared security solution for cross-chain interoperability. This works by enabling multiple protocols to derive security from a shared security zone made up of a single, dynamic set of Ethereum nodes. Operators can deploy the Lagrange State Committees in combination with restaking through EigenLayer, to address the challenges with current approaches to cross-chain interoperability.
Why we are onboarding Lagrange: As the first zero knowledge AVS on Eigenlayer, we are excited to work with an innovative solution like Lagrange. With 15+ committed professional operators and over $2 billion in pledged security by leading LRTs, we feel confident in supporting Lagrange in addressing the security question in cross-chain interoperability.
5. AltLayer: Bridging the Rollup Ecosystem
AltLayer offers two key services that are highly relevant to the Ethereum ecosystem. The first is their Rollup-as-a-Service (RaaS) solution, which enables the fast and customized deployment of rollups. The second, and more pertinent to Chorus One, is their "Restaked Rollups" – a vertically integrated suite of three AVSs that leverage EigenLayer's shared security to support decentralized rollups.
Why are we onboarding AltLayer: AltLayer's Restaked Rollup solution addresses key challenges facing decentralized rollups, such as the need for a decentralized sequencer (SQUAD), a robust verifier (VITAL), and fast finality (MACH). By onboarding this comprehensive suite of AVSs, starting with their MACH AVS in this iteration, we aim to provide critical infrastructure and support to the broader rollup ecosystem, accelerating the growth and adoption of scalable decentralized applications.
6. Witness Chain: Incentivizing Fraud Proofs for Optimistic Rollups
Optimistic rollups offer a promising path to Ethereum scalability, but their security properties have been limited by the lack of clear incentives for validators to diligently search for and submit fraud proofs. Witness Chain addresses this challenge with its Watchtower protocol – a programmable, trustless, and decentralized service that uses a novel "proof of diligence" mechanism to incentivize validators to support optimistic rollups.
Why are we onboarding Witness Chain: By onboarding Witness Chain as an AVS, we aim to continue our ongoing commitment to strengthening the security and decentralization of the L2 ecosystem, which is a crucial component of Ethereum's scalability roadmap. As optimistic rollups continue to gain traction, Witness Chain's services will play a vital role in ensuring the long-term viability and trust in these scaling solutions.
Stay tuned for Part 2 of this series, where we'll explore the additional exciting AVSs that Chorus One is onboarding to the EigenLayer network, further expanding the potential of the EigenLayer and Restaking ecosystem.
About Chorus One
Chorus One is one of the biggest institutional staking providers globally, operating infrastructure for 50+ Proof-of-Stake networks, including Ethereum, Cosmos, Solana, Avalanche, and Near, amongst others. Since 2018, we have been at the forefront of the PoS industry and now offer easy enterprise-grade staking solutions, industry-leading research, and also invest in some of the most cutting-edge protocols through Chorus Ventures. We are a team of over 50 passionate individuals spread throughout the globe who believe in the transformative power of blockchain technology.
EigenLayer recently upgraded to M2 Contract. This made it necessary for EigenPods created prior to this to be upgraded. So if your EigenPod was created prior to Stage 2, you will need to upgrade your EigenPod per the steps below. EigenPods that were created prior to M2 contract upgrades are required to have their balances reset to zero, then generate the proofs through the EigenLayer app in order to ensure proof accounting is accurate.
Note: This guide is useful for the native restaking users who want to delegate to Chorus One operator but don’t see any restaked tokens. This can happen when you restaked before the M2 upgrade. Following this guide you will start seeing your restaked tokens which can then subsequently be delegated to Chorus One
1. Go to https://app.eigenlayer.xyz/restake and connect your wallet

2. You will see a button to upgrade your EigenPod. Click Upgrade Eignepod
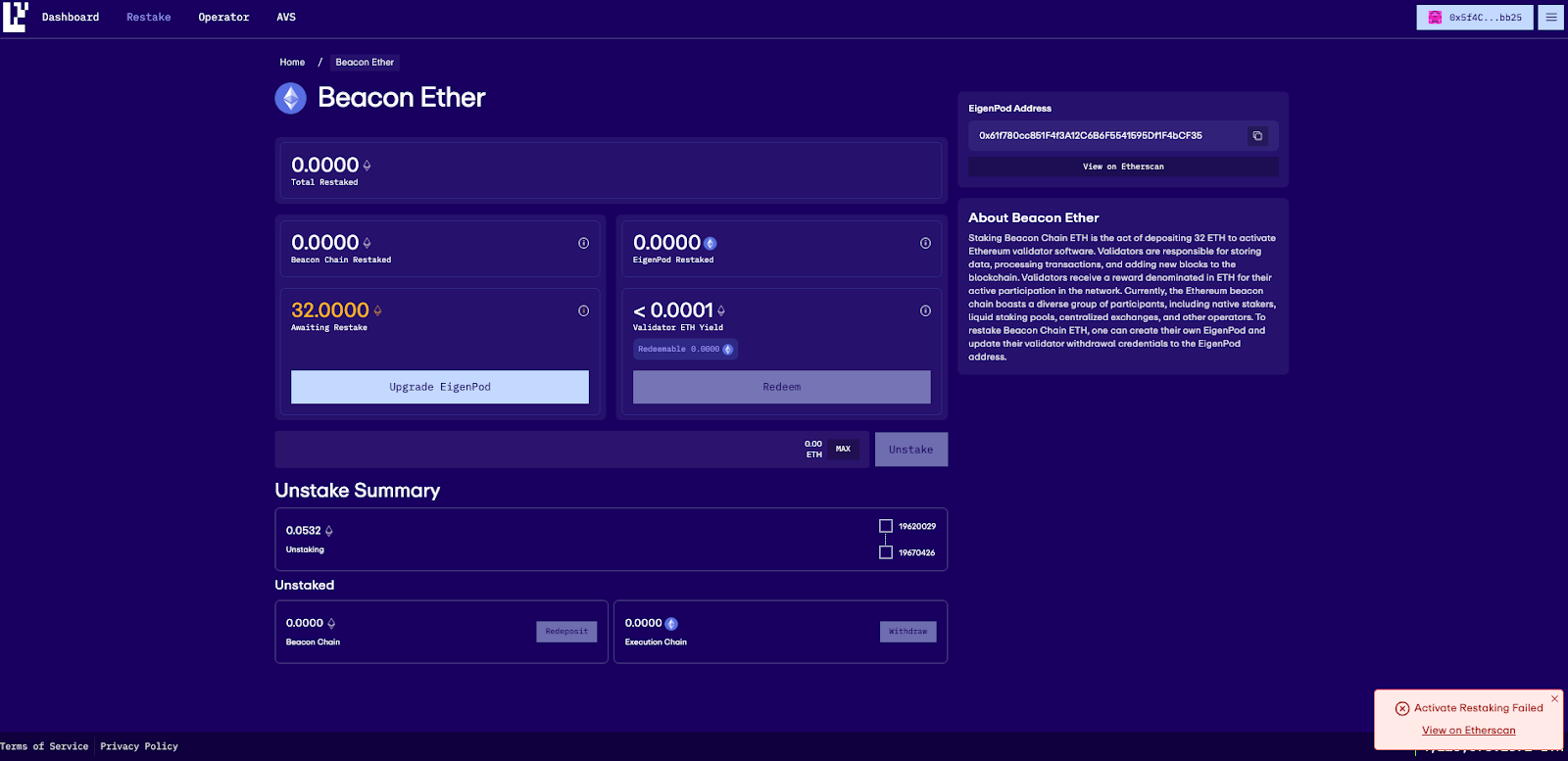
3. You will be shown a fee recipient warning, review the warning and click Continue


4. In case you have accrued any Consensus Rewards you might be asked to queue the withdrawal of the rewards before you can upgrade your EigenPod. Click Confirm.


5. Observe the Restaking Activated confirmation and explanation that Restaking will be available after the next beacon state update.


6. You can wait for the amount of time mentioned in the message. Come back later and hit the restake button to Restake your ETH

7. Once you restaked your ETH you can follow the steps in this delegation guide to delegate your restaked ETH to Chorus One operator

About Chorus One
Chorus One is one of the biggest institutional staking providers globally, operating infrastructure for 50+ Proof-of-Stake networks, including Ethereum, Cosmos, Solana, Avalanche, and Near, amongst others. Since 2018, we have been at the forefront of the PoS industry and now offer easy enterprise-grade staking solutions, industry-leading research, and also invest in some of the most cutting-edge protocols through Chorus Ventures. We are a team of over 50 passionate individuals spread throughout the globe who believe in the transformative power of blockchain technology.
We are thrilled to share the latest update from the EigenLayer ecosystem – a highly anticipated upgrade that promises to provide stakers with greater control and flexibility over their staked assets. Effective today, April 9th, the EigenLayer mainnet launch unlocks a suite of new features and functionalities for both stakers and node operators.
EigenLayer M2 builds upon the existing M1 contracts that have been operational on the Ethereum mainnet. This major upgrade introduces a crucial new capability: the ability for users to delegate their restaked Ethereum (ETH) or liquid staking tokens (LSTs) to the node operator of their choice.
And as one of the leading node operators, we’re thrilled to announce that users can now delegate their restaked Ethereum (ETH) and Liquid Staking Tokens (LSTs) to Chorus One!
Delegating to Chorus One is a seamless and secure experience. Users can easily delegate to Chorus one via any of the following options:

OPUS Pool is designed to make the restaking process effortless for our users. Here's a quick guide on how to delegate your assets through the OPUS Pool:
You can find the detailed, step-by-step guide for OPUS Pool here: https://chorus.one/articles/your-guide-to-opus-pool-stake-mint-oseth-and-restake-with-eigenlayer
Note: Restaking LSTs with EigenLayer is currently on hold and will resume once the deposit cap is raised. In the meantime, you are welcome to use OPUS Pool to stake any amount of ETH, mint osETH, and delegate your existing restaked LSTs.
.png)
Alternatively, you can directly delegate your assets to Chorus One via the EigenLayer dashboard. Here's how it works:
By choosing either OPUS Pool or Chorus One’s operator profile on the EigenLayer dashboard, you can seamlessly delegate your assets to Chorus One and benefit from our tailored approach, enhanced MEV rewards, and top-tier security measures.
Please Note: The upgrade doesn't yet allow Operators to earn yield for services provided to an AVS or to be at risk of slashing for Operator misbehaviors.
At the heart of the M2 upgrade is the introduction of delegation capabilities, empowering stakers to choose the node operator they wish to delegate their assets to. Specifically, the M2 contracts will enable users to deposit their Ethereum (ETH) or liquid staking tokens (LSTs) into EigenLayer through the StrategyManager (for LSTs) or the EigenPodManager (for beacon chain ETH). Additionally, stakers will now be able to withdraw their assets via the DelegationManager, regardless of the asset type.
For node operators, the M2 upgrade introduces the ability to opt-in to providing services for Actively Validator Services (AVSs) using the respective AVS's middleware contracts. However, the current iteration of the M2 contracts does not yet enable node operators to earn yield for the services they provide to AVSs or expose them to the risk of slashing for any potential misbehaviors.
In contrast to node operators who may prioritize onboarding as many AVSs as possible, Chorus One has adopted a more strategic and selective approach. Security is of paramount importance to us, and we meticulously vet each AVS before providing infrastructure support.
Our dedicated team thoroughly assesses the technical architecture and risk profile of every AVS under consideration. We leave no stone unturned, carefully evaluating factors such as the robustness of their systems, the soundness of their security protocols, and their overall risk appetite. Only those AVSs that meet our stringent criteria are granted access to our staking infrastructure.
This selective approach ensures that our users can have the utmost confidence in the management of their assets. By entrusting their stakes to Chorus One, our customers can rest assured that their funds are being handled with the highest levels of diligence and care, safeguarded by our rigorous vetting process.
To learn more about Chorus One's tailored approach to restaking, we encourage you to reach out to our team at staking@chorus.one. Our team will be happy to answer any questions you might have.
Ready to get started? Visit OPUS Pool and follow our detailed guide to easily delegate your assets to Chorus One.
The technical details of the M2 upgrade can be found in the official EigenLayer documentation, available at https://github.com/Layr-Labs/eigenlayer-contracts/tree/dev/docs. As the EigenLayer ecosystem continues to evolve, this latest milestone towards Mainnet promises to empower stakers and node operators alike, ushering in a new era of flexibility and control.
About Chorus One
Chorus One is one of the biggest institutional staking providers globally, operating infrastructure for 50+ Proof-of-Stake networks, including Ethereum, Cosmos, Solana, Avalanche, and Near, amongst others. Since 2018, we have been at the forefront of the PoS industry and now offer easy enterprise-grade staking solutions, industry-leading research, and also invest in some of the most cutting-edge protocols through Chorus Ventures. We are a team of over 50 passionate individuals spread throughout the globe who believe in the transformative power of blockchain technology.
OPUS Pool, powered by Stakewise, enables you to stake any amount of ETH with Chorus One, mint osETH, and directly deposit into EigenLayer in one flow. With the launch of Delegation on Eigenlayer you can now easily delegate your restaked position to Chorus One with a single click of a button.
Not only that, users may bring in liquid staking tokens (LST's) from any external platform, including osETH, wbETH, rETH, cbETH, stETH, oETH , ankrETH , swETH, ETHx, and directly restake with EigenLayer if they wish to do so.
Start using OPUS Pool to stake ETH. Visit https://opus.chorus.one/pool/stake/
OPUS Pool facilitates greater participation in securing the network but also allows a wider range of Chorus One stakers to earn rewards and gain access to a suite of benefits, including top-tier MEV yields, low fees, and the assurance of enterprise-grade security, among others.
Opus Pool brings in a host of benefits for users. Let’s take a brief look at what you stand to gain.
1. Stake any amount of ETH and mint osETH
OPUS Pool enables a user to stake any amount of ETH (no 32 ETH minimum requirements) and receive rewards instantly. Additionally, users have the ability to mint osETH, a liquid staking derivative, and use it in DeFi or deposit into EigenLayer to gain additional rewards directly on OPUS Pool in one go.
2. Low Fees
OPUS Pool sets itself apart from current liquid staking protocols by offering users the advantage of highly competitive staking fees. At just 5%, our fees are among the lowest in the industry, making it more accessible for a broader spectrum of users to stake their ETH and earn rewards.
3. Top-tier MEV Rewards
As pioneers in MEV research, our latest ace, Adagio - an MEV-Boost client, allows for more efficient interactions with Ethereum’s transaction supply chain, directly enhancing MEV rewards for stakers. Fully integrated with OPUS Pool validators, Adagio ensures that anyone staking on OPUS Pool can benefit from these increased MEV rewards.
Want to learn more about Adagio and its mechanics? Read all about it here.
4. Restake osETH, stETH, cbETH, rETH with EigenLayer in One Go.
OPUS Pool offers a unique feature: users can deposit not only osETH minted through OPUS Pool but also liquid staking derivatives like stETH, cbETH, and rETH minted on other platforms, directly into EigenLayer.
The OPUS SDK: In addition to the benefits mentioned above, our Institutional clients can leverage the OPUS SDK to integrate ETH staking directly into their UI, providing their customers with all the benefits of the OPUS Pool seamlessly. To know more, please reach out to staking@chorus.one.
Now, let’s move on to the guide.
1. To start staking, head over to https://opus.chorus.one/pool/stake/ and connect your wallet.

2. Select your desired wallet. Note that you can use WalletConnect if you want to connect through Ledger Live.

3. Once connected, make sure you are on the Stake tab. You can see all the tabs on the left-hand-side of the screen.

3. Enter the amount you would like to stake. You can see the estimated amount of daily/monthly/yearly rewards you will earn with this amount of stake.

4. Hit Confirm and Stake button and sign the transaction in your wallet

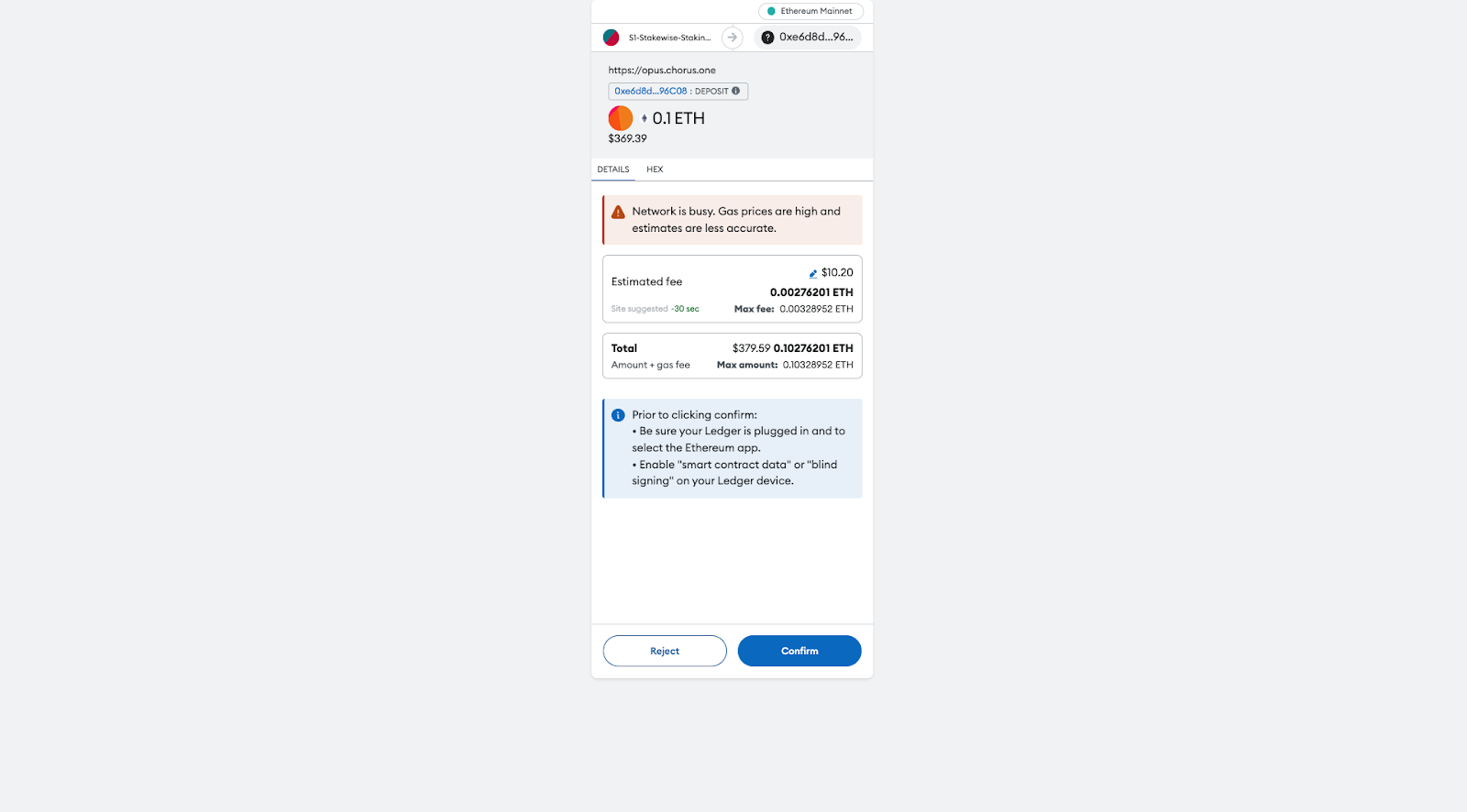
5. Congratulations, you have now successfully staked your ETH! As a next step you can go to the dashboard to look at the summary of your staking position or you could head over to the Mint osETH tab to mint some liquid staking tokens for your staked position.


2. Enter the amount of ETH you would like to use to mint osETH.

3. Click on Mint button and approve the transaction in your wallet

4. Congratulations! You have successfully minted osETH for your staked ETH. You can now head over to the dashboard to view your staked position and osETH summary. You can alternatively restake your osETH to Eigenlayer.

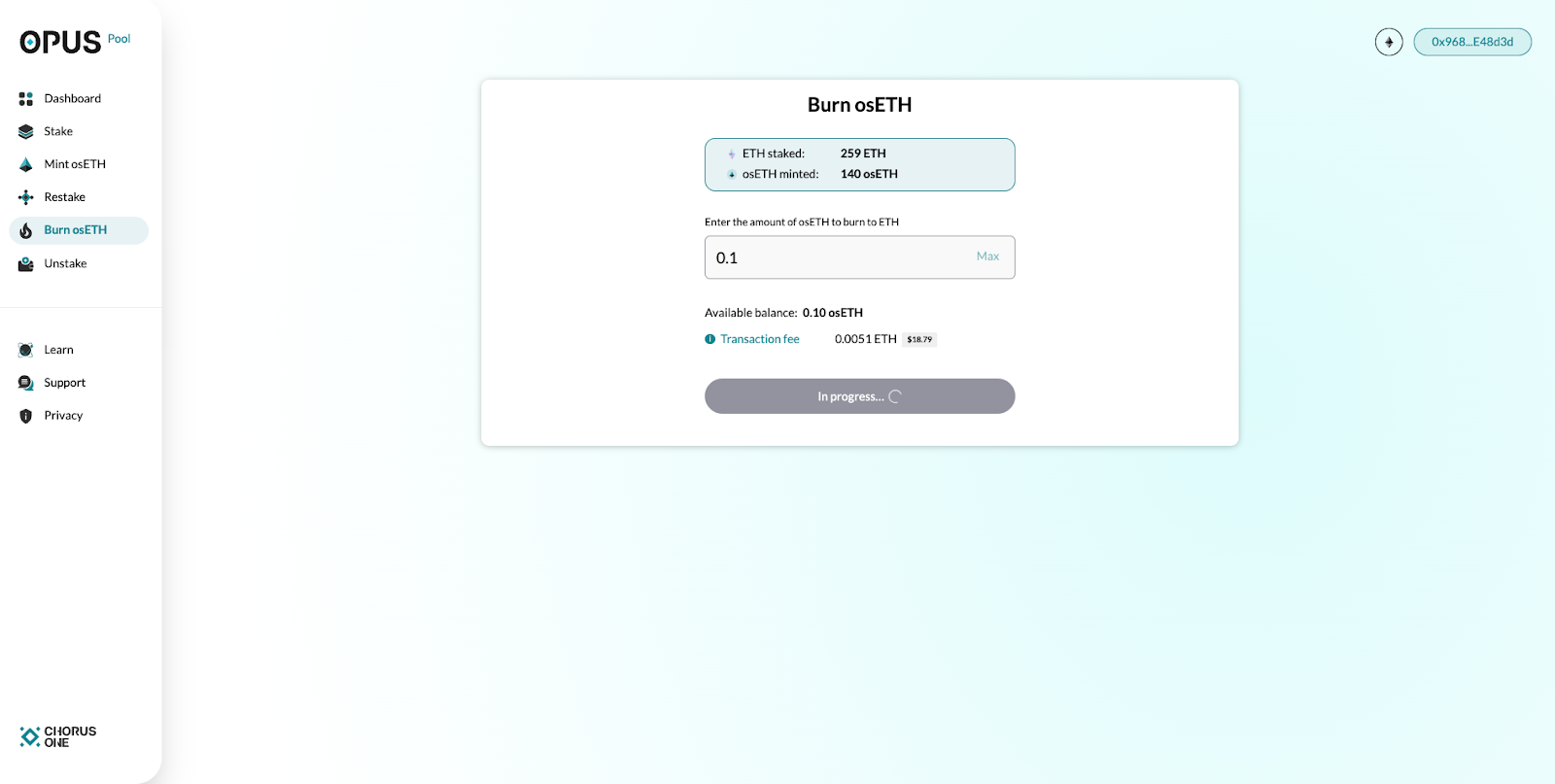
5. In case you want to reverse the minting process, you can burn your osETH to get ETH back. Select the Burn osETH tab on the left menu, enter the amount you would like to burn and hit Burn

6. Once you click on Burn, you will be prompted to sign the transaction in your wallet. Upon signing, you will have successfully completed the burn process

1. To deposit your osETH, or any accepted staked ETH into EigenLayer including wbETH, rETH, cbETH, stETH, oETH , ankrETH , swETH, ETHx, click on ‘Restake’ in the menu bar and select the asset you wish to deposit.
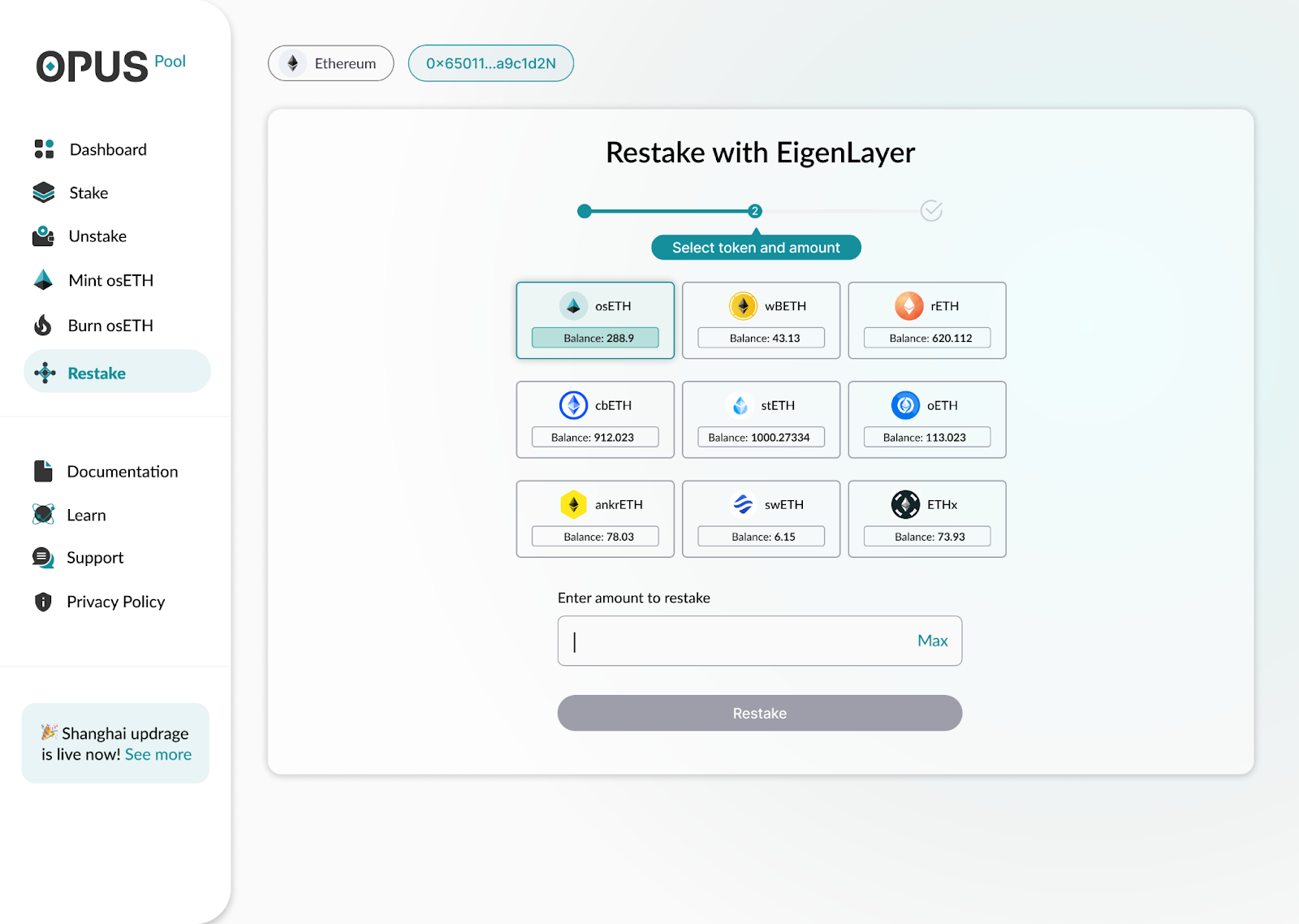
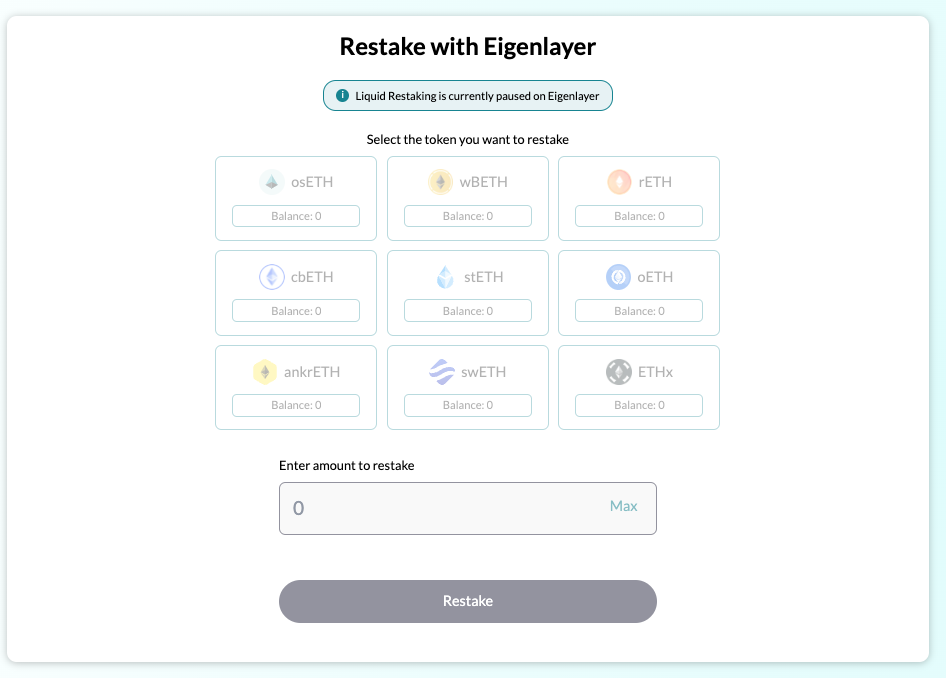
3. In case deposits into Eigenlayer are live you may select the LST that you possess, enter the desired amount that you would like to restake and hit the Restake button

4. You will be prompted to sign the transaction in your wallet. Once you do that, you will have successfully restaked to Eigenlayer. You can go back to the dashboard to delegate your assets to Chorus One or view the summary of your staked position.

1. Eigenlayer recently launched their delegation manager contract and enabled staker delegations. This will allow anyone with restaked ETH or restaked LSTs to delegate their restaked position to an operator of their choice. To delegate your stake to Chorus One, head over to the dashboard by clicking on the Dashboard button on the left navigation bar.

2. In case you have not already delegated to another operator, you can click on the Delegate to Chorus One button.

3. You will be prompted to sign a transaction in your wallet. Once you sign, you will see the following screen. Congratulations your restake position is now successfully delegated


4. Alternative, you can go directly to Eigenlayer App - https://app.eigenlayer.xyz/operator and search for Chorus One operator

5. Click on the Chorus One card that shows up

6. If you have not previously delegated to any operator, you will see a Delegate button on the right of the screen. You will also see a message “You currently have a restaked balance that is not delegated”. Click on the delegate button and sign the transaction in the wallet.
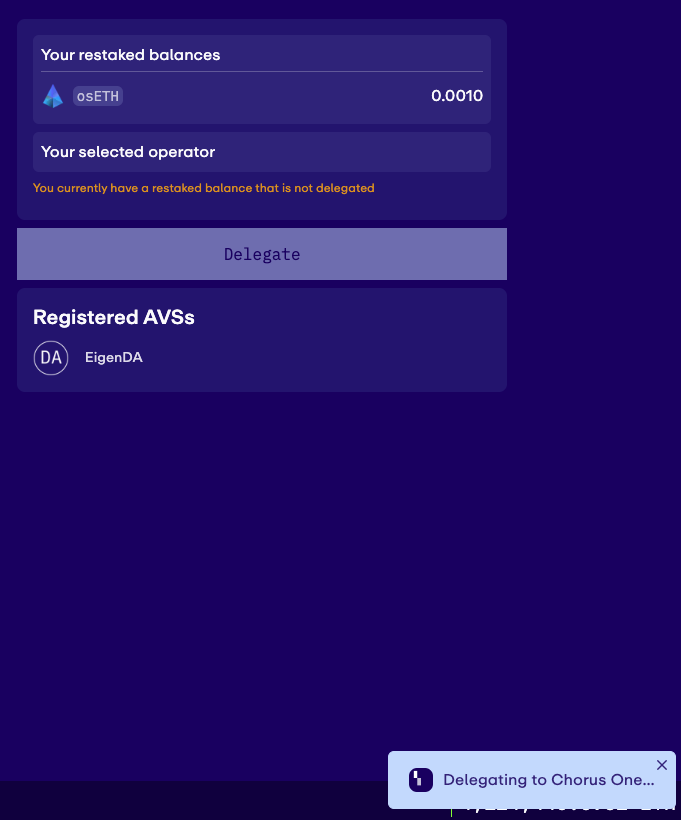
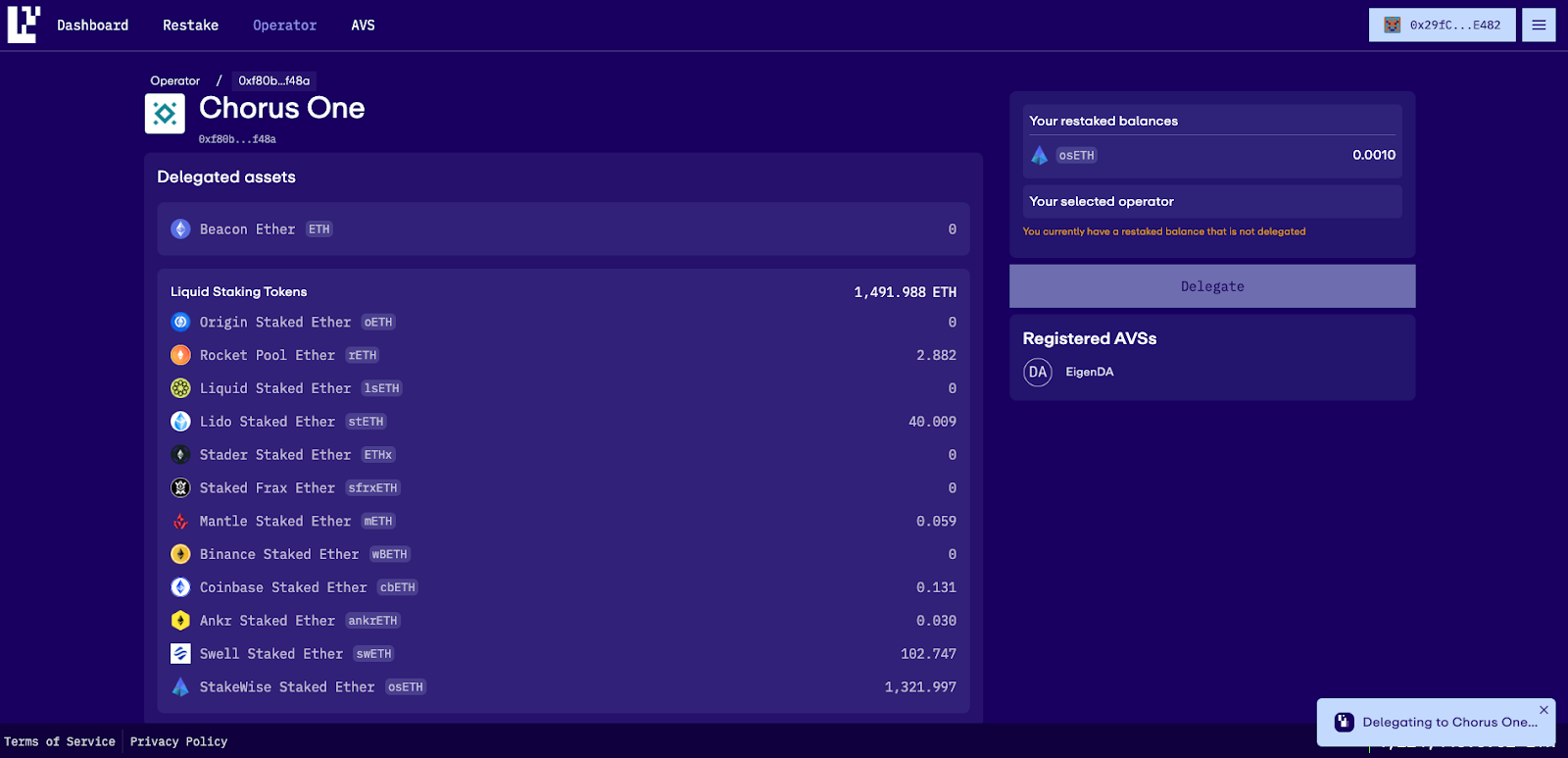
7. Congratulations you have successfully delegated your stake

Switching node operators means moving your restaked funds from supporting the original node operator supported AVSs to Chorus One supported AVSs.

Note: Switching operator requires you to sign 3 transactions. The first transaction queues the withdrawal of your restaked assets. This is a prerequisite of the Undelegation function. The second transaction undelegates your restaked position. The final transaction delegates to Chorus One. You will need to restake your assets again after you switch the operator. You may not be able to restake your assets until Eigenlayer reopens the deposit cap.
2. Click on Switch Operator and sign the transaction in the wallet

3. You will see another transaction pop up to undelegate from the operator. Sign the undelegation transaction

4. Finally you will see your wallet prompt you to sign the delegation transaction which delegates to Chorus One. This is the final transaction in this process


5. Once the transaction is confirmed you will have successfully delegated to Chorus One. Make sure to go back to the restaking tab and start restaking your assets


2. Enter the amount of ETH you would like to unstake and hit the Unstake button

Note: If you minted osETH at any point any time against your staked position, you might have to burn that amount to unstake all your ETH
3. You will be prompted to sign the unstake transaction in your wallet. You have successfully unstaked your position. Once you unstake your ETH enters the withdrawal queue. You will see a progress bar right below the success message that lets you know the status of your withdrawable stake. Once it becomes ready for withdrawal you will see a button to claim the stake back into your wallet.

4. You can come back to the Unstake tab at a later point and check the status of your withdrawal.
Resources
About Chorus One
Chorus One is one of the biggest institutional staking providers globally, operating infrastructure for 50+ Proof-of-Stake networks, including Ethereum, Cosmos, Solana, Avalanche, and Near, amongst others. Since 2018, we have been at the forefront of the PoS industry and now offer easy enterprise-grade staking solutions, industry-leading research, and also invest in some of the most cutting-edge protocols through Chorus Ventures. We are a team of over 50 passionate individuals spread throughout the globe who believe in the transformative power of blockchain technology.